|
|
|
|
News The Project Technology RoboSpatium Contribute Subject index Download Responses Games Gadgets Contact <<< Secure Comunication-Terminal (SCT) Microcontroller-Set >>> SCT Version 2The video demonstrating secure communication via InternetA bit more comfort
The core components are an Arduino UNO, a PS/2 keyboard and a display with a resolution of 320x240 pixels. Doesn't look very elegant, but works quite well. The upcoming version should be more compact. Parts listWhen buying components via the affiliate partner links I have listed in the table (or through the banners on my pages) you help to keep my my projects going - many thanks!Clicking on the links does not mean you have to buy - you can simply browse through the pages ;-) Of course, supporting my freely accessible educational platform without shopping but by making a donation or becoming a Patreon also works. Many thanks to everyone who already sent me an obol! If you know more parts that are good for building circuits shown on this page, please leave a comment.
Electronics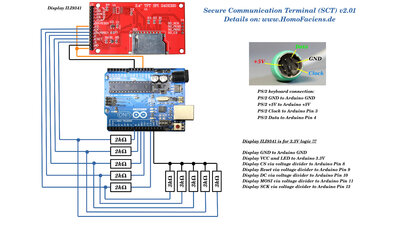
Wiring of the components. EncryptionIn order to make the text, entered in plain text on the microcontroller, unreadable for unauthorized persons, the characters must be encrypted. A very old method is the Caesar shift, named after Julius Caesar, in whose lifetime, which dates from 100 to 44 BC, this encryption method was already known. With this method, the required characters are listed in a table and shifted by a fixed value. In the example shown here, the characters of the text "HELLO WORLD!" shifted 3 characters to the right, resulting in the encrypted term "KHOOR3ZRUOGB". There is no message to be found in it. At first glance, however, it is noticeable that the letter "O" occurs 3 times in the encrypted text, for example, just as often as the letter "L" in "HELLO WORLD!". In principle, there are only as many ways to encrypt the original text as there are characters in the table. In our case, that's 39. For today's computers, decoding is no problem even without knowing the secret key character and is done in fractions of a second.On the target system, the text is decrypted by shifting the letters of "KHOOR3ZRUOGB" letter by letter 3 characters to the left in the table, resulting in the source text "HELLO WORLD!". 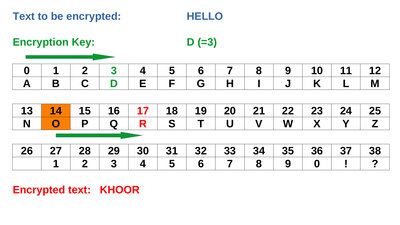
Caesar shift: Click on the drawing to see an animated version. An extension of the method consists in not only shifting all characters by the same, fixed value, but using a keyword that specifies different position shifts. The longer that keyword, the trickier it gets to decipher the original text without knowing the keyword. With the appropriate computing effort, however, this can now be done quite quickly, whenever the key is significantly shorter than the text to be sent. Deciphering becomes impossible if the text is shorter or at least as long as the stored key - even quantum computers will not change that! 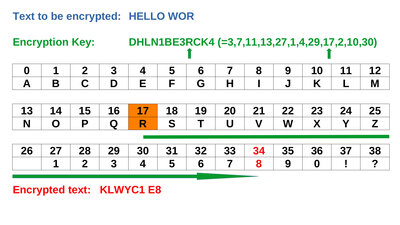
Vernam chiffre: Click on the drawing to see an animated version. Encrypt on the command lineAs promised in the video, here is a small Python script that uses the same, not really secret, secret key as the Arduino sketch:
Save the Python script above as "encrypt.py" In line 6, change the text between the quotes. Don't uses more than 170 characters! Save the changes and run the script with: Python encrypt.py You must now send the file "encrypted-message.zip" that is generated by the script to my email address safe_001(at)HomoFaciens.de. I can then read your "secret" message on my terminal. Can't wait to get your message! Secure keysA requirement for secure encryption is that the key consists of a random distribution of all available characters and is as long as possible compared to the transmitted text. Ideally, the key is at least as long as the plaint ext. In the software example for this chapter, the key is:"ThisIsNoReallySecretKeyNorIsItStrong!DontSayYouWereNotWarned!" A byte is the basic unit of characters in the computing world. This consists of 8 bits and can therefore be used to represent up to 256 different characters. The not really good keyword uses only 27 of them. In addition, many characters appear more than once. If the double characters are removed, the result is: "ThisINoRealyScrtKyNng!DYuWd" In each language, the available letters occur with different incidence. This is a starting point for deciphering poorly encrypted messages. I will talk about secure key generation in a coming chapter. It should be clear that the key: "DDDDDDDDDDDD" fulfills the condition of being as long as the text "HELLO WORLD!", but is in principle as weak as the Caesar cipher. 
Keys with a length of several billion characters fit on a micro SD card - so you can type until your fingers fall off, without anyone being able to understand the message if it is intercepted. The card reader with the secret key must of course be inside our castle, and so connected directly to the microcontroller. Messages encrypted in this way can only be read by people that have a copy of this key. The key exchange should therefore not take place over the Internet, because if this byte sequence becomes public, you can as well write your messages on the outer walls of your house. Another advantage of encrypted messaging is that the original text cannot be modified during transmission: From a point where bytes have been inserted or removed, the text becomes unreadable - if bytes are overwritten, the corresponding passage becomes data garbage. Messages sent unencrypted are completely discarded by the microcontroller - spam is automatically excluded, only group members with a suitable key can write to the terminal. The encryption acts like a signature at the same time. Neither the two PCs that are connected to the Arduinos on the start and target system, nor any computer in between on the Internet, can decode the message; only the start and target addresses, the time of transmission and the size of the file are known. USB interface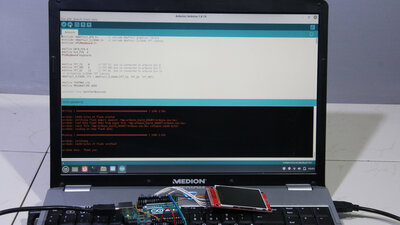
If the data is transferred between the microcontroller and the PC via the USB interface, as in shown here, it must be taken into account that the program code and the key can be read by the PC! Furthermore, the code on the microcontroller can be manipulated. This is definitely a weak point of the system! Although the microcontroller can be secured by setting special memory cells (=fuses) or by replacing the "normal" bootloader by a special one that prevents programming via Arduino IDE, but these steps can also be reset via software. In a following version I will therefore put another microcontroller between the laptop and the microcontroller serving as a "castle". The data exchange between these two microcontrollers then takes place via GPIOs. In this way, access to the program memory of the microcontroller, which is to be regarded as secure, can be completely blocked. If you use a Raspberry Pi as an Internet PC, thewre is no need fo that "intermediate" microcontroller because data can be exchanged directly via the GPIOs of the Raspberry Pi. However, as long as this terminal is not used by millions of people, it is rather unlikely that the USB vulnerability will really be exploited... Software/DownloadThe software for this terminal works, but is not the "holy grail" in terms of usability:The program that handles the communication between the PC and Arduino must be started from the Linux command line after the Arduino has been connected to the USB interface. Although it is relatively easy to enter text using the computer keyboard, there is no automatic spelling correction and the cursor cannot be moved using either a mouse or the arrow keys. Text is always entered at the end and you can only delete either everything with the "Esc" key or only character by character starting from the end. There is room for improvement, but the Arduino still has enough free program memory to implement some of it. Installation details can be found in the readme.txt of the download package (1.0MB), which also contains the circuit diagram. <<< Secure Comunication-Terminal (SCT) Microcontroller-Set >>> News The Project Technology RoboSpatium Contribute Subject index Archives Download Responses Games Links Gadgets Contact Imprint |
|
|